Biggest Crypto Hacks: Full List of Scams of All Time

In 2024 alone, cryptocurrency scams and hacks caused more than a billion of dollars in losses worldwide. One of the biggest breaches, the DMM Exchange hack, wiped out $305 million in investor funds, shaking user confidence in Centralized Finance (CeFi). With the crypto industry growing rapidly, so does the sophistication of cybercriminals. In this article, we’ll explore some of the biggest crypto hacks and scams to date, common vulnerabilities, and actionable strategies to protect yourself from similar incidents.

While cryptocurrencies offer unprecedented financial freedom and opportunities, users need to take responsibility for safeguarding their investments.
Understanding risks is crucial for anyone participating in the crypto space. Whether you trade, invest, or simply store assets, knowing how scams operate can help protect your holdings. Unfortunately, the decentralized nature of crypto makes it a prime target for malicious actors, and recovering stolen funds can be incredibly challenging.
Article contents
Overview of Crypto Security
The rapid growth of the cryptocurrency market has made security a top priority for users and platforms alike. While blockchain technology offers a high level of transparency and decentralization, it does not make the ecosystem immune to threats. Users must understand the essential elements of crypto security, such as wallets, exchanges, and private keys, to manage their investments effectively. A proactive approach to security is critical, as even minor oversights can result in significant losses. Let’s have a closer look at basic security measures:
- Blockchain technology is the foundation of most cryptocurrencies. It serves as a decentralized ledger where transactions are recorded across numerous independent nodes. This structure ensures that once a transaction is confirmed, it becomes immutable—meaning it cannot be altered or reversed. This transparency builds trust, but the decentralized nature also presents challenges in terms of user responsibility and regulatory oversight. With no central authority managing the blockchain, users must take ownership of their security practices.
- Cryptocurrency wallets are essential tools for storing digital assets, and there are two main types: hot wallets and cold wallets. Hot wallets, such as mobile apps or web-based wallets, are connected to the internet, offering convenience but exposing users to potential cyberattacks. Cold wallets, like hardware wallets, remain offline and are far more secure, making them ideal for long-term asset storage. Both types of wallets rely on private keys, which are the gateway to accessing funds. If a private key is lost or compromised, the associated assets become inaccessible, often permanently.
- Crypto exchanges are another critical component of the ecosystem. Centralized exchanges (CEX) handle users’ funds but require a high degree of trust, as evidenced by past incidents like the collapse of FTX. Decentralized exchanges (DEX) allow users to trade directly from their wallets, giving them more control over their assets. However, DEX platforms can expose users to other risks, such as scams like rug pulls. Selecting reputable, secure exchanges is essential for minimizing vulnerabilities.
- Multi-factor authentication (MFA), particularly two-factor authentication (2FA), is a fundamental security measure. It requires users to verify their identity through two steps—typically a password and an authentication code—adding a layer of protection. End-to-end encryption is also essential for exchanges and wallets, ensuring that user data remains secure, even if the system is breached. These measures together significantly reduce the likelihood of unauthorised access.
The unique nature of cryptocurrency transactions makes security paramount. Once a transaction is confirmed on the blockchain, it cannot be reversed, meaning that stolen funds are almost impossible to recover. Unlike traditional banks, most cryptocurrencies are not insured, leaving users responsible for their losses. Furthermore, the global nature of the crypto space attracts cybercriminals from all over the world, making it difficult to trace and recover stolen assets.
Biggest Crypto Hacks & Scams to Know About
The following cases illustrate how vulnerabilities in the crypto ecosystem have led to catastrophic losses. From exchange breaches to Ponzi schemes, each incident reveals valuable lessons for investors and traders.
Mt. Gox Hack (2011–2014)
Mt. Gox was once the largest Bitcoin exchange, handling over 70% of all Bitcoin transactions. However, between 2011 and 2014, hackers exploited the platform’s security flaws, ultimately stealing 850,000 BTC. At the time, the stolen funds were valued at $450 million, but today their worth would exceed billions.
The hack severely damaged the reputation of cryptocurrency exchanges and triggered increased scrutiny from regulators worldwide. Mt. Gox filed for bankruptcy in 2014. This event highlighted the need for exchanges to adopt advanced security protocols and the importance of not storing large sums of crypto on centralized platforms.
OneCoin Ponzi Scheme (2014–2017)
The OneCoin scam, orchestrated by Ruja Ignatova—dubbed the “Crypto Queen”—is considered one of the largest Ponzi schemes in history. The scheme lured investors by promising huge returns, claiming to be a revolutionary cryptocurrency. However, OneCoin had no blockchain technology backing it, exposing it as a fraudulent operation.
At its peak, OneCoin defrauded investors of over $4 billion. Ignatova disappeared in 2017, and her whereabouts remain unknown. This case underscores the importance of transparency in crypto projects and serves as a warning against investing in schemes that promise unrealistic returns.
Bitfinex Hack (2016)
In 2016, the Bitfinex exchange suffered a security breach that resulted in the theft of nearly 120,000 BTC, worth approximately $72 million at the time. The hack had a significant impact on the platform, forcing Bitfinex to compensate affected users by issuing a recovery token.
This incident revealed the importance of robust security measures, such as multi-signature wallets, which could have mitigated the damage. It also encouraged exchanges to prioritize user education about securing personal accounts and diversifying asset storage.
BitConnect Ponzi Scheme (2016–2018)
BitConnect gained popularity by promising high daily returns through a lending program, attracting thousands of investors. However, in 2018, the platform collapsed, leaving investors with billions in losses. Authorities pursued legal actions against those involved, and while some funds were recovered, many investors were left empty-handed.
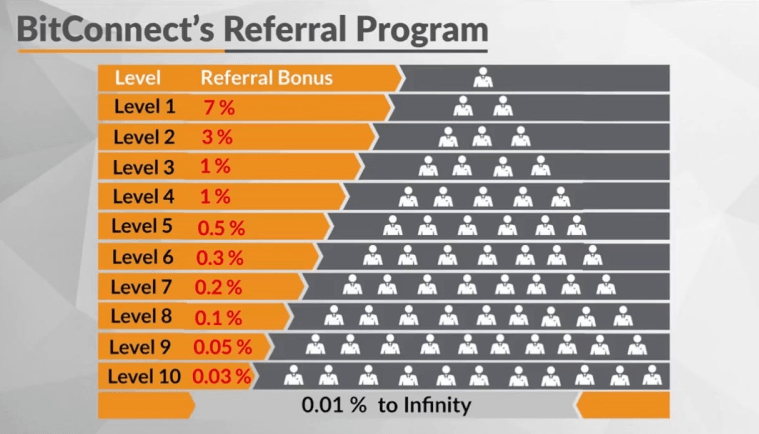
BitConnect’s rise and fall highlighted the role of social media influencers in spreading risky schemes. It also exposed the dangers of multi-level marketing (MLM) structures in the crypto industry.
PlusToken Scam (2018–2019)
PlusToken was a wallet and investment scheme targeting Asian investors, promising high returns. The scam defrauded users of over $2 billion before collapsing in 2019. Although several arrests were made in China, much of the stolen funds remain unrecovered.
The fallout from PlusToken increased regulatory scrutiny of crypto exchanges and wallet providers, raising awareness about the risks of investing in platforms with opaque operations.
QuadrigaCX Incident (2019)
QuadrigaCX, a Canadian exchange, became the center of controversy when its founder, Gerald Cotten, reportedly died unexpectedly, taking with him the private keys to $190 million in user funds. The incident sparked investigations, revealing questionable business practices and leaving many to suspect foul play.

The QuadrigaCX case stressed the importance of transparency and key management, encouraging users to store their funds in wallets they control rather than relying solely on exchanges.
Africrypt Scam (2021)
Brothers Raees and Ameer Cajee allegedly defrauded South African investors of $3.6 billion through Africrypt, a crypto investment platform. The brothers claimed the platform had been hacked and subsequently disappeared, leading to a public outcry and demands for better regulatory oversight in South Africa.
This scam underscored the need for strong legal frameworks to protect investors and prevent fraudulent activities in the crypto space.
FTX Collapse (2022)
FTX, once among the largest cryptocurrency exchanges, collapsed in 2022 following revelations of mismanagement and misuse of customer funds. Billions of dollars were lost, and the incident sent shockwaves through the crypto industry. The failure of FTX led to intensified calls for stricter regulations on exchanges and greater transparency.

Legal proceedings against former CEO Sam Bankman-Fried are ongoing, with regulators and investors closely watching the outcome. This case serves as a stark reminder of the importance of exchange accountability and user vigilance.
BtcTurk Hack (June 2024)
In June 2024, Turkish exchange BtcTurk lost $55 million in a sophisticated cyberattack. The breach exploited security vulnerabilities within the platform, raising concerns about the safety of funds held on centralized exchanges.
The incident prompted regulatory responses in Turkey and highlighted the importance of regular security audits to prevent such breaches.
DMM Exchange Hack (May 2024)
In May 2024, the Japanese exchange DMM experienced one of the largest security breaches in recent history, losing approximately $305 million. The hack occurred due to a compromised private key, which granted attackers access to a large portion of the platform’s funds. This incident not only affected DMM’s users but also raised serious concerns about the reliability and security protocols of centralized financial (CeFi) platforms.
The breach was a stark reminder of the importance of private key management. Reports indicated that the private key was not properly segmented or protected, allowing hackers to exploit this vulnerability and drain significant assets. The incident led to a freeze on DMM’s services as the exchange launched an internal investigation. However, the damage to the platform’s reputation was already done, with investors questioning whether their funds were safe on similar centralized exchanges.
Types of Cryptocurrency Hacks
The methods hackers use to exploit the crypto space are constantly evolving. Below are some of the most common types of attacks that users and platforms encounter, along with insights on how they operate, their impact, and strategies for protection.
Phishing Attacks and Social Engineering
Phishing attacks are among the most widespread threats in the crypto space. Hackers impersonate trusted entities—such as wallet providers or exchanges—through fake websites, emails, or messages, tricking users into sharing sensitive information like private keys or login credentials. These attacks often come in the form of urgent requests, such as claims of account issues or security breaches, prompting users to act without verifying the legitimacy of the communication.
Phishing and social engineering attacks succeed due to human error, and even experienced users can fall victim. Once hackers obtain private keys or passwords, they can drain wallets instantly, leaving users with little to no recourse. To avoid these attacks, users must be cautious when clicking on links, verify the authenticity of all communications, and activate two-factor authentication (2FA) wherever possible.
Rug Pulls in DeFi Projects
Rug pulls occur when developers of Decentralized Finance (DeFi) projects abruptly abandon their platforms after collecting significant investments from users. In many cases, developers launch new tokens or liquidity pools, build hype around them, and then disappear with the funds once investors deposit large sums. These scams have become increasingly common, especially during the rapid rise of DeFi.
The impact of rug pulls is often devastating, wiping out user investments and eroding trust in DeFi platforms. To minimize risk, investors should conduct thorough research on projects, looking for transparency in development teams and verifying if the code is audited by reputable firms.
SIM Swapping and Account Takeovers
SIM swapping is a targeted attack where hackers take control of a user’s phone number by convincing mobile carriers to transfer it to a SIM card under their control. Once they have access, attackers can intercept SMS-based authentication codes, gaining entry to crypto wallets or exchange accounts.
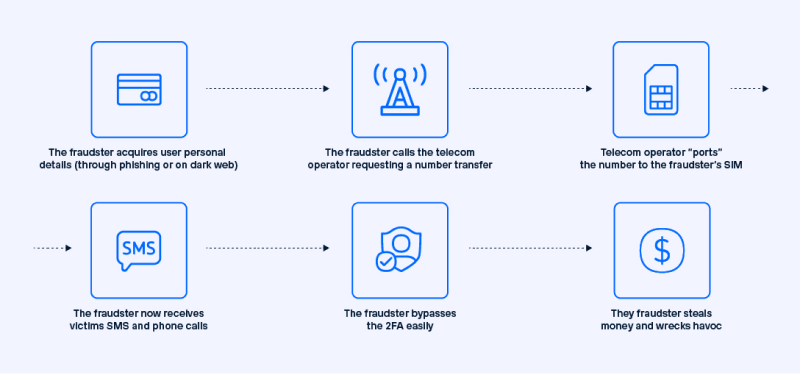
Account takeovers through SIM swaps are particularly harmful because they bypass 2FA if it relies on SMS. Victims of these attacks often suffer substantial financial losses. To protect against SIM swapping, users should enable app-based authentication methods instead of SMS and consider adding additional security layers, such as biometric verification or carrier-level PINs.
Pump and Dump Schemes
Pump and dump schemes manipulate the prices of lesser-known cryptocurrencies by artificially inflating their value through coordinated buying. Once the price peaks, organizers sell their holdings, causing the value to plummet and leaving unsuspecting investors with worthless tokens. These schemes thrive on social media, where influencers or anonymous groups encourage followers to buy specific tokens.
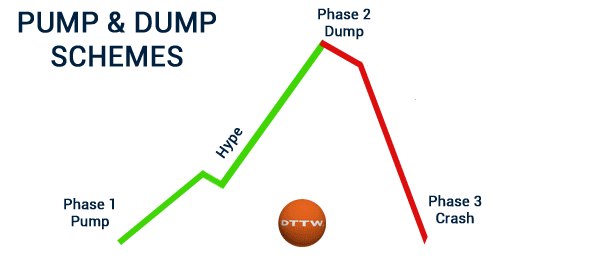
Investors caught in pump-and-dump schemes can suffer severe losses. Recognizing these scams requires skepticism towards sudden price surges without solid fundamentals. Diversifying investments and sticking to established projects can help reduce exposure to such schemes.
AI-Driven Deepfake Scams
With advancements in artificial intelligence, deepfake technology has become a tool for scammers. Hackers use deepfakes to impersonate well-known personalities, promoting fake crypto schemes through videos or live streams. Cases of fraudulent celebrity endorsements have surged by 245% in recent years, tricking users into investing in fraudulent platforms.

The best defense against deepfake scams is vigilance. Users should verify endorsements through official channels and avoid making decisions based on videos or messages without conducting independent research. Staying informed about the latest scam tactics can also help users identify and avoid deepfakes.
How to Protect Yourself from Crypto Hacks & Scams?
Protecting your crypto assets requires a combination of secure practices, smart decision-making, and constant vigilance. Below are some key strategies to safeguard your investments and reduce the risk of falling victim to hacks and scams.
Use Secure Wallets
Storing crypto assets in secure wallets is crucial. Hardware wallets (cold wallets) are the safest option, as they store private keys offline, making them immune to online attacks. Hot wallets provide easy access for frequent transactions but are more vulnerable to hacks. A combination of both—storing most assets in a hardware wallet and keeping a small amount in a hot wallet—offers an effective balance between security and convenience.
Enable Two-Factor Authentication (2FA)
2FA adds an extra layer of protection by requiring users to provide a second form of verification, such as a code from an authenticator app or SMS. It is essential to enable 2FA on all crypto-related accounts, including exchanges and wallets. App-based authenticators are preferred over SMS, as SIM-swapping attacks can compromise text message security.
Verify Exchange Security
Before choosing a cryptocurrency exchange, research its security protocols. Look for platforms with multi-signature wallets, cold storage solutions, and end-to-end encryption. User reviews and security audits can also provide insights into the reliability of an exchange. Avoid exchanges with a history of breaches or poor user feedback regarding fund security.
Stay Informed and Updated
The crypto sector evolves rapidly, and new threats emerge frequently. Staying informed about the latest security practices and scam alerts is essential. Following reputable crypto news websites, forums, and social media accounts can help you stay ahead of potential risks.
Be Skeptical of Unrealistic Promises
If an investment opportunity seems too good to be true, it probably is. Scammers often promise high returns with minimal risk to lure victims. Always conduct your own research and avoid platforms that lack transparency or have limited information about their operations.
Implementing these protective measures can significantly reduce your risk of becoming a victim of crypto hacks or scams. However, maintaining security is an ongoing process, requiring continuous effort and vigilance.
Common Mistakes Leading to Crypto Vulnerabilities
Even well-meaning users can unintentionally expose themselves to significant risks by neglecting basic security practices. Below are some of the most common mistakes that lead to vulnerabilities, along with tips on how to avoid them.
Poor Password Management
Weak passwords or reusing the same password across multiple platforms create easy entry points for hackers. If one account is compromised, others quickly follow. Users should create unique, complex passwords for every crypto-related service. Using a password manager helps keep track of passwords securely and ensures they are not reused.
Ignoring Software Updates
Crypto wallets, apps, and exchanges regularly release software updates to fix vulnerabilities and enhance security. Outdated software leaves users exposed to known exploits. It is crucial to keep all wallets and apps up to date. Enable automatic updates whenever possible to ensure you are always running the latest version.
Lack of Diversification
Holding all crypto assets in one place, such as a single exchange or wallet, increases the risk of catastrophic loss in the event of a hack or scam. Diversifying your holdings across multiple platforms reduces exposure. Cold wallets should store long-term investments, while only smaller amounts should be left on exchanges for trading purposes.
Overlooking Regulatory Compliance
Investing in platforms that lack proper regulatory oversight can be risky. Scams often flourish in jurisdictions with weak regulations or enforcement. Verifying the regulatory status of an exchange or project is essential to ensure it operates transparently. Platforms that comply with Know Your Customer (KYC) and Anti-Money Laundering (AML) regulations are generally safer, although they may still carry risks.
Conclusion
The world of cryptocurrency offers exciting opportunities, but it also comes with serious risks. The high-profile hacks and scams discussed—ranging from the Mt. Gox hack to the FTX collapse—serve as stark reminders of the importance of robust security practices..
By understanding the types of threats that exist investors can better protect their assets. Adopting secure habits is essential. Avoiding common mistakes can greatly reduce the risk of falling victim to fraud or theft.
The responsibility for securing crypto investments lies primarily with the user. While exchanges and platforms can implement security measures, individuals must also be proactive. Diversifying holdings and verifying the legitimacy of projects can go a long way in safeguarding assets.
In the crypto space, staying informed and practicing good security habits is not just recommended—it’s necessary. Share this article with others to help raise awareness and encourage smart, secure participation in the crypto world!
Follow us on Medium, Twitter, Telegram, YouTube, and Publish0x to stay updated about the latest news on StealthEX and the rest of the crypto world.
Don’t forget to do your research before buying any crypto. The views and opinions expressed in this article are solely those of the author.
Bitcoin crypto hack cryptocurrency FTX exchange scamRecent Articles on Cryptocurrency
 Aergo Price Prediction: Can AERGO Coin Reach $100?
Aergo Price Prediction: Can AERGO Coin Reach $100?  Kaspa Price Prediction: Can KAS Coin Reach $1?
Kaspa Price Prediction: Can KAS Coin Reach $1? 